PDF of articles here: Are we the New Digital Soylent Green - PDF
("Soylent Green Is People").
When “No Means No” is not enough.
Note: This article is availble in Video format with soothing background music [Link].
Informed Consent Video [Rumble Link]
Data is the new Oil is the new rally cry for investors. They do share a common challenge. An oil spill can be devastating to an organisation as well as the environment.
A data spill (or data breach) can be just as devastating to an organisation and its customers.
So, why do we handle data so poorly?
Cyber security is top news today. Too many organisations think they are either too small to matter or their data isn't significant because they are not the only ones that have it.
The bad news is neither is true.
In recent months, I have written about
AI,
Chatbots,
Data Sovereignty,
Data In Transit and more. What do these areas have in common?
Information.

In today’s world, we gather information, both structured (databases etc.) and unstructured (documents etc.) at an alarming rate. Due to the global digital transformation, the line between structured and unstructured is already becoming blurred. As a result, the challenges of managing all of this information responsibly can become incrementally more challenging. However, this can be more easily navigated with a responsible approach to digital transformation.
So, how does this impact you and your organization? The answer boils down to one focal point.
Consent – more than just a definition in the legislation.
Consent under GDRP and other privacy legislation has a narrow definition. However, it is important to view “Consent” in its larger dictionary definition when looking at information under your care, custody and/or control.
Understanding cyber-security, physical security, legal and compliance rules is a complex task. However, by taking each area and applying one simple question will help clarify what you can, cannot, should or should not do.
Ask yourself;
Would the customer/owner of the information truly “consent” to what you, or someone else is about to do (or has done) with the information?
This could be anything from an unauthorized breach by an internal/external party (cyber-security) to a new use of the information such as using AI/Machine Learning/Deep analysis or even third-party disclosure (compliance/legal) for something other than the reason it was originally gathered.
We have all heard the cry
“No Means No". However, in real life, you don’t actually have to say
“No” to mean
“NO”. This short (2:50) video by
Blue Seat Studios illustrates Consent in the non digital world.
Link: Consent a cup of tea solves everything.
I'm going to need an explicit YES.
In the digital world,
“NO” is usually inferred
AND you need explicit consent to show otherwise at every step of the information management, analysis and transformation. Be prepared to show a time and date stamped explicit acknowledgement of everything from buying the tea bags, to washing the cups (and everything in between or after) in the above example, especially if you suddenly want to make coffee!

Article 4 of GDPR (11),
“(11) 'consent' of the data subject means any freely given , specific , informed and unambiguous indication of the data subject's wishes by which he or she, by a statement or by a clear affirmative action, signifies agreement to the processing of personal data relating to him or her;”
Although the wording may be slightly different in each privacy legislation, the intent is the same in most cases.
To further complicate matters, most privacy legislation has focused on identifying 'personal data'. For GDPR, this has been expanded to;
“means any information relating to an identified or identifiable natural person ('data subject'); an identifiable natural person is one who can be identified, directly or indirectly, in particular by reference to an identifier such as a name, an identification number, location data, an online identifier or to one or more factors specific to the physical, physiological, genetic, mental, economic, cultural or social identity of that natural person; ”
“Once more unto the breach, dear friends”

There are many forms of breach beyond having your data stolen by a foreign hacker. Effectively an unauthorized access or use of the data you have custody and/or control is deemed a breach. You should assume that no matter what your privacy policy might state, customers do not consent to a breach.
Just because they don't drink the tea, doesn't mean you can give it to someone else or leave it out for someone else to drink.

Ask yourself;
- Has your customer truly consented to storing their data in the current location (#datasovereignty)?
- Would your customer be happy if a foreign government or third party accessed their information without their knowledge?
- Would a customer be happy with you using the data in new and exciting ways?
- Does your customer (or you) truly know what data you are collecting, or is being collected by systems you have in place?
- Has your customer consented to storing their data in the current location?
- Would your customer be happy if a foreign government or third party accessed their information without their CONSENT?
Think about hosted systems that may be gathering and extrapolating from your customers’ use of your systems hosted or supported by others i.e. the digital supply chain for information;
- e-Commerce
- Web Sites
- Apps (voice, data, video)
- Chatbots
- Third Party WiFi hosts
Can they hear me now? (Who’s listening?)

The IoT devices we now see proliferating our every-day life are always listening and collecting data to 'make your life better'. However, did the client who just walked in to your office, consent to their voice or other data being captured, stored and used by a third party?
- Think home/office automation and the IoT (Google Home, Siri, Amazon Echo and more.)
Do you really know what information you have in your
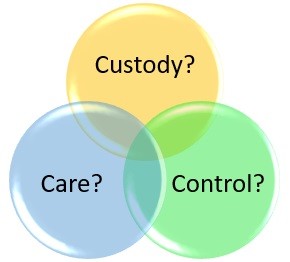
If not, then you probably should rethink your process for obtaining informed consent, change what data you collect, the way you collect it and how it is stored/accessed.
Do you know what to do if you discover a breach?
- Clue: Paying hackers and trying to cover it up is an 'uber' bad decision!

Third parties may be collecting data at various levels as a bi product of the services they provide. Do you know what they gather and what they do with that data? Do your clients or other individuals who use your systems or premises know that they may have their digital identities or other personal information captured? An unintentional (or intentional) disclosure of this information to a third party could be a breach.
Don't be a weak link in the supply chain and don't be a victim of another weak link.
Is an expectation of privacy reasonable anymore?

If you are in a private location or you have provided data willingly, you may have a reasonable expectation of privacy. Is that realistic anymore in a consistently monitored and digitally connected world? If not, what are the implications to the new privacy laws and society as a whole?
Are we even trying to maintain our privacy anymore?
When we discover that our personal data has been compromised, we cry from the rooftops about the injustice. Yet we have probably provided that same information (and more) on social media, at restaurants and over the phone many times before without even a passing thought. This information is collated, analyzed and extrapolated from us in milliseconds.
This does not excuse lax security and privacy in business…
but it should make us think.
We ALL have a role in the privacy equation and it is an important one.
David Dickson is a Consulting C.E.O. and owner at DKS DATA
(www.dksdata.com). Our Services
Remember to eat your Soylent Greens.











